A note from the team: we’re continually looking for possible applications of ZKAPs in a variety of scenarios. If there is a product or project you’re working on that you would like to test ZKAPs with, don’t hesitate to get in touch!
Last month, our team, the Least Authoritarians, gave two presentations on ZKAPs—zero-knowledge access passes. Although we created ZKAPs to better address the access-control issue in Tahoe-LAFS for the development of PrivateStorage, we see many possibilities for the use of ZKAPs to help protect user privacy in other services that need to accept online payments.
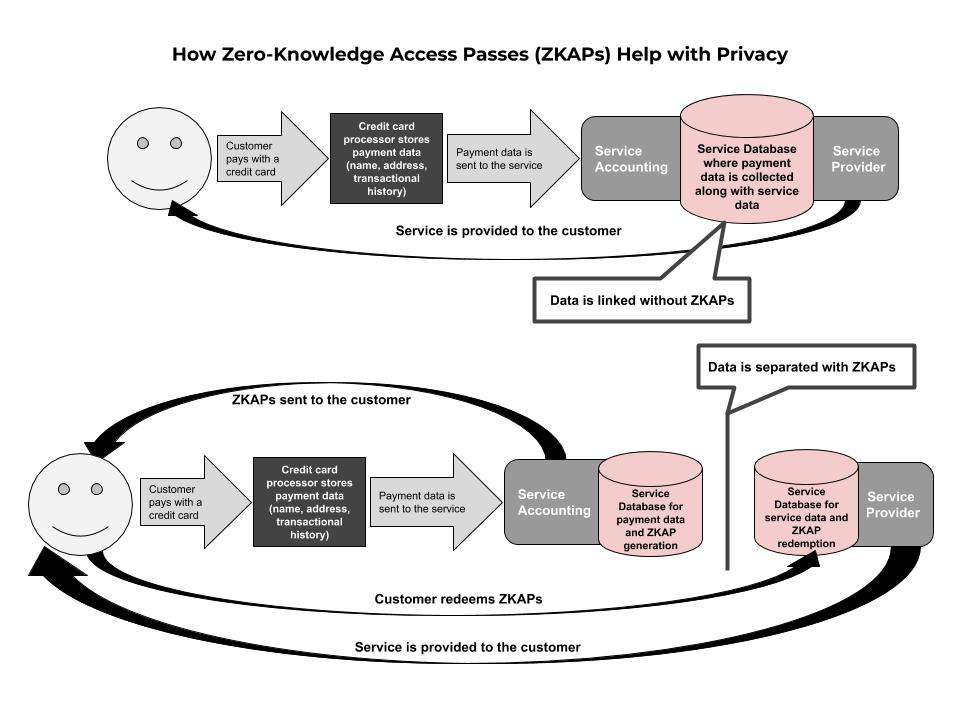
The use of ZKAPs can help facilitate an online exchange of value while disconnecting the payment and service data that is gathered on customers. This is very helpful in use cases where mixing these data points is not in the best interest of the company offering the service, such as ours. While collecting personal data can be incredibly valuable to some services (“data is the new oil”) it can just as often be a liability to others (“data is toxic waste”).
In addition, disconnecting payment from service data can provide value to customers. The company offering a service can still know through payment data who its customers are. But, customers may not want that company to know how they use the service—specifically, for the company to tie behavior that they observe (service data) to an individual name. This can be relevant for file storage services, but also for any other kind of use that may be privacy-sensitive, such as medical advice or even newspaper consumption.
For ZKAPs, we designed a variation of Privacy Pass—a zero knowledge cryptographic protocol with proof-of-payment, instead of proof-of-humanness .
While in Privacy Pass the use of CAPTCHAs is checked, in this system payment is verified on the Payment Server to provide service, which is when ZKAPs are created and distributed to the user. After creation, ZKAPs are requested and checked in the ZKAPs Authorizer. This privacy-preserving infrastructure maintains separation and simplicity.
For generating ZKAPs we created and used Python [and Haskell] bindings to Brave’s Privacy Pass library. Brave’s implementation of Privacy Pass uses the Ristretto group, which uses a Rust implementation for group operations on Ristretto. It was through the use of thoughtful open source resources that we were able to modify Privacy Pass to develop ZKAPs.
We gave two different talks on ZKAPs last month, take a look if you would like to learn more:
- zkSummit on March 31st, by Anna Kaplan—video not yet public, tickets available to watch full program of talks. (YouTube / Slides)
- Zeal Zcash Community Call (below) on March 31st, by Chris Wood & Jean-Paul Calderone (YouTube / Slides)
Update July 2021:
You can read the Whitepaper here and watch our talks on ZKAPs here. If you would like to talk to us about using ZKAPs as a standalone service, email us at contactus@leastauthority.com. If you want to see ZKAPs in action, sign up to be notified of the launch of PrivateStorage later this year (we will delete your email address after the notification).
